Prolific writer who wrote “Gift of the Magi”, “Turning of the Screw”, “Ulysses”, and “Black Water”
Corporate Anti-P2P Legal Catch-22
Some corporations attempt to enforce their copyrights by monitoring and interfering with P2P copies of their media. This is most common with movies and TV shows, especially new and popular ones.
There are two primary ways that they try to disrupt and inhibit copying, and usually will outsource the effort to third-parties instead of doing it themselves.
- They usually monitor P2P traffic of files related to their copyrights. They use modified/hacked P2P clients to join and participate in the traffic, posing as sources for the file(s). Then when someone connects to them in an attempt to download part of the file, they log the person’s IP address and send an abuse letter to the ISP associated with the IP along with the time and filename. Sometimes they also merely spy on (“lurk”) and copy the peer list without posing as sources, though they prefer to trick people into actually connecting so that they can “prove” an attempt was made to obtain the file.
- They sometimes also try to sabotage the downloads by again, posing as sources for the file(s), but uploading junk data so that the people trying to download the files don’t get the file (at least not as fast) and waste their bandwidth.
Some of these are obvious like when a swarm has thousands of seeds within seconds of being released or when a bunch of episodes are released at the same time and/or before they have aired. Sometimes however it is not so obvious and they will commit much fewer resources to sabotaging and logging the file, especially for older, less popular media.
What they don’t seem to realize is that there is a serious problem with their attempts to prevent users from downloading the files, and their efforts to legally enforce copyright on them is specious.
There are two main issues with their anti-P2P efforts:
- If the anti-P2P computers provide users with junk data, then they cannot say that the user has downloaded a bootleg copy of the media, they downloaded junk which is not illegal. The only connection the junk data has with the copyrighted material is the filename which again is not illegal, otherwise every website that mentions the materials name would be illegal.
- If the anti-P2P computers actually provide real parts of the file, then there’s a few problems:
- The data that the user obtained is not actually copyrighted material, it is simply a block of essentially meaningless data. It only takes on any meaning when combined with a lot of other blocks of meaningless data. This can be true of many things. For example, while an entire book could be copyrighted, the individual words (or even more to the point, the letters) are not copyrighted. Therefore you cannot prosecute someone for receiving a bunch of random words from people even if you just happen to assemble them in an order that turns them into a story.
- If the anti-P2P computer is providing real data that can be combined to make a real file, then they have to have gotten it themselves. While they may have been granted rights to the media, it is unlikely that they are allowed to obtain and distribute illegal copies of the media.
- By distributing illegal copies of the media, the anti-P2P is either performing an illegal act, or else it is legitimizing the distribution of the file, and converting it from illegal to legal. Moreover, by participating in P2P, they cannot make the argument that they are entitled to the distribution rights of the file, including “ripped” copies while everybody else is not, because P2P is not distributed from a single, central point.
Therefore, anyone who gets an abuse letter from a company alleging that they were “caught” downloading copyrighted materials can refute it. They can demand the proof that they were engaging in the bootlegging which will likely come in the form of a “log” that shows their IP address, a filename, and a timestamp. They can then employ the above arguments to demonstrated that either they did not actually have the real file and instead had junk data and/or that they did not engaging in bootlegging at all because the company was actually granting permission to get the file by providing the file to people when they participated in P2P.
The psychology of “bubble porn”
An amusing meme on the Internet is the concept of “bubble porn”, also known as “Mormon porn”. The idea is to take a photo of someone who is scantily clad, but not nude, and mask out the clothing, leaving only bare skin exposed. The result is that the person in the photo now looks to be naked.
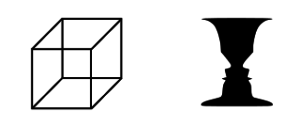
This phenomenon is actually a manifestation of Gestalt theory, specifically, the principal of closure, the property of emergence, and the principals of continuity and past experience. In psychology, there are several principals/laws/properties of the Gestalt theory of perception. There is no definitive set of Gestalt principals, and the theory itself is debated, but below are a selection of properties. Some of them are similar while some are overridden by others. In general, they cause things being seen to be perceived as units. Most of these are for visual perception, but proximity also works in time. That is, when two things occur close to each other, they are perceived to be connected, hence the perception of one thing causing another even if it did not.
In the case of bubble-porn, by masking out the clothing, the brain tries to fill in the blanks with what information is available, and since the information available is the surrounding skin, and since we have experience with what bodies look like, the mind perceives the person as being naked under the masks. As if celebrities didn’t already have enough to worry about with fake nude photos (and as of 2017, AI-generated fake videos).


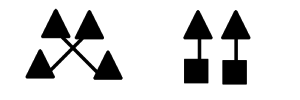

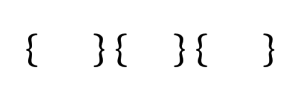




Nails on a Chalkboard
In the History Channel documentary How the Earth Made Man, they list how various aspects and attributes in human biology and behavior can be explained as remnants of the evolution of humans and the Earth.
One of the qualities they explained was the reason that humans find the sound of nails scraping on a chalkboard to be so grating and causing us to cringe. Unfortunately they got it completely wrong.
Their explanation is that our primate ancestors who lived in trees and avoided predators would use a screeching sound to warn of danger, and so we now find that sound to be disturbing. It sounds like a good explanation but it is specious.
It is true that humans find the sound of nails grating on a chalkboard to be unnerving, but it is not the sound itself that is disturbing, it is the knowledge of what it feels like. To wit, scraping a lenticular with our nails produces a completely different noise, but the same cringe-inducing shudder. It is the physical sensation that repulses us so much.
Next time your hands are slick with oil or soap, scrape your fingernails along the ridges of the fingerprints on your thumb. There is pretty much no noise at all, yet the feeling is just awful. Clearly it is the sensation, that is, the vibration that is so aversive.
Something about the tactile feel of quick, small, sharp, repetitive vibrations is extremely uncomfortable and undesirable to humans, and certain sounds like nails on a chalkboard remind us of that.
Don’t Bother with Aftershave
Most men have gotten in the habit of splashing on some aftershave after, well, shaving. The reason is pretty obvious: after shaving, the skin is raw and susceptible to infection; aftershave kills any bacteria on the face, keeping it clean and infection-free.
This makes sense, but the active ingredient in aftershave is alcohol. The scents and perfumes in aftershave serves no practical purpose (in fact, it could even attract bugs if you are in a climate with a lot of flies, mosquitoes, etc.)
Therefore, there is no reason to spend a lot of money on what amounts to a small bottle of smelly alcohol. Instead, you can spend a dollar or two to buy a larger bottle of rubbing alcohol which provides at least the same level of antiseptic (often more since isopropyl alcohol is available in up to 99% concentrations). In addition to getting a larger quantity of stronger alcohol, it also has the benefit that it evaporates in seconds, leaving a nice, clean, refreshing, and odorless face.
Of course some people may think that the scent is the point to aftershave and prefer to smell for hours after shaving, but rubbing alcohol is superior in several ways, so for the rest of us, it is a great alternative.
Squirrels Check Structural Integrity of Nuts to Determine Which to Bury and Which to Eat
Abstract
Squirrels (and chipmunks, and likely other rodents) examine nuts to determine which to bury and which to eat.
Question
Why do squirrels bury nuts? Why do they prefer in-shell nuts to shelled nuts?
Background
Living in a townhouse for quite a few years, Melody Soroudi has had the opportunity to be up close and personal with squirrels (primarily black and grey), as well as other related rodents such as chipmunks. She has been feeding them shelled nuts for years and later added in-shell nuts, or what David Suzuki calls “five-dollar bills”.
Feeding them in-shell nuts created an interesting behavior in the squirrels: they began to bury the nuts much more often than when they were getting only shelled nuts. Why?
Obviously they bury them in order to store them for later use (like the Aesop’s Fable about the Ant and the Grasshopper), specifically for use in the spring when plants are dead or dried up and not fruiting. But surely they cannot bury all of the nuts, they must eat during the summer as well.
The fact is that they do, but they are selective and discerning about which nuts they eat and which they bury.
Observations
If you watch squirrels closely, the behavior becomes apparent. When they get a hold of a nut, they turn it over and over in their hands while examining it with their mouths. If they detect significant cracks or broken or missing pieces of shell, they rip it open and eat the nut(s) inside. If they detect the shell to be structurally intact, they bury it. They do not eat nuts whose shells have a small crack along a seam which are still “closed”, only those they deem to be “compromised”.
This is a logical move because a nut that is compromised is like a coffin with a hole, it will be invaded by bugs and worms and the like and not only get covered in soil, but decompose, or even germinate and start to grow. In fact, nuts that squirrels have lost and forgotten is one method by which some plants reproduce; the shell eventually dissolves and the nuts inside (assuming that they are not roasted) begin to grow. Squirrels are essentially farmers who plant seeds.
Followup Question
Why do squirrels prefer in-shell nuts to shelled nuts? Obviously an in-shell nut provides less energy and nutrients than shelled nuts.
The ones that have the shell only contain two (or occasionally three, but sometimes even just one) nut. They also take up more space and thus can be packed less efficiently, wasting room on shells and air. Also, they require extra work to remove the shell.
Shelled nuts on the other hand require no extra work to get at the valuable part and can be packed better to put more food in less space.
Clearly shelled nuts are more optimal than in-shell nuts. So why do squirrels and other rodents prefer the shells? Why do they prefer to store food for the future than to use it now like some animals do?
This is simple to explain. Larger animals like bears and camels have the physical space to store the energy for future use by plumping up and storing fat in their bodies, however, small rodents do not have that physical capacity, so they must store the food externally in their homes or in the ground.
In addition, large animals tend not to move too much, and thus consume less energy while foraging than small animals like rodents do. Squirrels and chipmunks travel long distances from their nests to look for nuts and run up and down trees and such and thus burn a lot of energy just to get food. Therefore they need to accumulate and store a lot of food for future use.
Buying Time When Buried Alive
Being buried alive is a frightening thing for anyone. There’s plenty of ways it can happen; a few common ones include:
- Being assumed dead when actually not (e.g., tetrodotoxin)
- Being buried by a bad guy (or as a hostage)
- Coming back to life (as a zombie, through magic, etc.)
If you return from the dead, then there’s not a whole lot to be done, you really just have to dig your way out. Depending on how you came back, you may or may not be at risk of dying again, so oxygen deprivation may or may not be an issue.
If you were believed to be dead, then you are probably in trouble because nobody is looking for you.
But what if you were buried by a bad guy? In the movie Buried, Ryan Reynolds’ character is taken hostage and while they wait for the ransom, he is stashed in a box underground. Towards the end of the first season of The Following, an FBI agent is buried alive as a way to torture the main character.
How can you survive? How can you buy time until you are rescued? Obviously oxygen is going to be your most immediate problem. You need to conserve oxygen as much as possible.
First and foremost, the best way to conserve oxygen is simply to sleep. Breathing rate drops significantly when we sleep, so sleeping will help to use as little oxygen as possible.
Another way to buy time is to create more oxygen. How do you create oxygen? Simple; just split water.
If you have some source of electricity like a phone battery, then you can split water molecules (H2O) into hydrogen and oxygen molecules. Simply take the battery out, use some sort of conductive write like a pin to create “electrodes” and hold them against the two ends of the battery. Then put the two electrodes into the water and let the electricity split water molecules into breathable air.
You may be wondering where you can get water in a box underground. Assuming that the box isn’t conveniently leaking groundwater, then you have saliva which has a lot of water, but urine has even more. Pee into the corner and put the electrodes in there. You should be able to get enough oxygen to buy at least some time until rescue arrives.
There are a few caveats with this however:
- When you split water, you create both oxygen and hydrogen. Hydrogen is not breathable and anyone who knows of the Hindenburg will tell you that it is extremely combustible, so any spark (like from a short-circuit from a battery!) could blow up you and your casket.
- There are plenty of other compounds in urine like urea (CO(NH2)2) as well as Chlorine, Sodium, and Potassium. It may be possible to create other harmful gases when electrolysing urine.
- You will want to make sure to use your phone (if possible) to call for help before pulling out the battery. If you actually do have reception and your phone has GPS, then it’s best to just leave it on and sleep.
- one more thing…
It may be dangerous to electrolyse urine, but if you’re about to die anyway, then it may be worth the chance to buy some time.
Chocolate: The Universal Food
Chocolate is a very curious food stuff. Not only does it taste great, have a master-key to the brain’s pleasure center, and have various health benefits (all in moderation of course), but it is a universal food, meaning that it goes well with a wide variety of other foods. Short of perhaps salt, chocolate may very well hold the record for the most combinations. Some of the most popular include chocolate+
- Milk
- Ice-cream
- Butter
- Coffee
- Toast (e.g., a chocolate spread)
- Strawberry
- Banana
- Orange
- Raisins
- Nuts (e.g., almonds)
- Peanut-butter
- Coconut
- Chili Peppers (mole sauce)
Obviously it doesn’t go with everything (chocolate doesn’t go particularly well with grapes, tomatoes, or potatoes, nor is it ideal with eggs or even apples), but it goes with many things. If you are a “gastronaut” or an experimental chef, then try chocolate in different ways to find new and exciting culinary experiences.
Maximizing the 32-bit 4GB RAM Limit
If you have a 32-bit system with 4GB installed, you can reduce the amount of RAM that gets wasted and make some more of it available by opening the BIOS configuration and reducing the AGP aperture setting to the minimum amount (e.g., 4MB).
Note: this may affect 3D graphics performance, so it is best for systems which don’t do 3D gaming or systems with video-cards that have a lot of video memory.
Hotplugging SATA Drives
The SATA specification allows for SATA drives to be hotpluggable.
This usually allows manufacturers to create external drives that can be hot-swapped (via USB) more easily than with IDE drives. However, this usually also works for internal drives.
If you have an internal SATA drive (hard-drive, DVD drive, etc.) which is not connected to the motherboard and boot up Windows, not surprisingly, it will not show up in the Device Manager. If you then connect the drive’s data cable to the motherboard (and perhaps optionally) do a re-scan in Device Manager, the drive will then show up because the SATA controller detected the drive and made it visible to Windows.
This is great. If you accidentally forget to connect a SATA drive to the system and don’t want to shut down or want to create your own sort of external drive, this feature is very helpful.
Unfortunately, like most things, the pros come with cons. In this case, while the newly connected drive becomes visible to Windows and is usable, it will likely have poor performance. Windows loads the drivers for the drive on boot, so if you connect the drive after booting, instead of loading the tuned, high-performance drivers for it, it will end up using simple, low-speed access to (i.e., it will not use UDMA). You can see this as extremely slow transfers to/from the drive. If you do this with a DVD burner for example, it will be limited to ~2x even if you set it burn at 8x or whatever). You can also see this effect in the Task Manager’s Performance tab; the CPU load will jump when you use the drive, but no processes will spike because the load is coming from the kernel. This may or may not also occur in Linux or Mac.
So while SATA allows hotplugging drives, it doesn’t mean it will work well. Manufacturers will still need to provide a shim to allow for maximum performance and OS developers will need to better detect newly attached SATA drives and load the drivers at runtime.